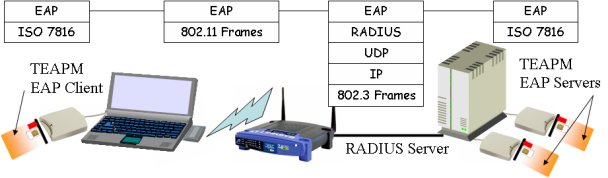
What is a TEAPM ?
TEAPMs are tamper resistant devices (smartcards) that run EAP client
and/or server applications.
A public javacard implementation, based on the
OpenEapSmartcard
platform is available on the WEB.
Multiple client and server entities may simultaneously work in a 64
KB device.
What are the TEAPMs benefits ?
- Security modules dedicated to IP devices.
- They are used for access controls and users'
authentication in Wi-Fi or WiMAX networks and VPN infrastructures
- Independent of any operating system (Windows,
LINUX,…).
- TEAPM applications run in tamper resistant devices,
such as smartcards. They may be designed for javacards, and therefore are
independent of any manufacturers.
- Highly secure Authentication Servers.
- Smartcards enabled RADIUS servers are docking hosts
that work in collaboration with multiple TEAPMs. This architecture is scalable,
and may be used in existing Wi-Fi infrastructure, supporting a great number
of clients.
- Privacy and Tracability .
- IP tracability is generally understanding as the record
of data traffic associated to a particular IP address. This address is linked
to an human user by means of the authentication procedure. Privacy, in
the tracability context, means that the network client remains anonymous,
its identity is never exposed to an untrusted party. The TEAPM architecture
enables highly secure authentication but guaranties user's anonymity.
- We currenty propose an efficient mechanism for identity
protection over EAP-TLS, a
presentation
was made at the IETF 66th in Montreal
- Remote administration.
- TEAPMs may be remotely and securely managed, and support
the following services
- Cancellation of credentials, such as X509 certificates
and associated private keys. Smartcards cloning is extremely difficult,
in consequence there is only one physical instance of these entities. The
ability to remotely block their use, is an important security requirement,
in a distributed PKI environment.
- Updating of credentials. There is a need to guaranty
continuity or extension of customer subscriptions. This demand is fulfilled
by replacing or adding information elements that control services availability.
- Downloading of new applications. Authentication
protocols may evolve and include new functionalities. In that case, the
software is transparently updated, e.g. without TEAPM bearers interaction.
Other details can be found in this
white paper
.
Some publications.
- Urien, P, Dandjinou, M, “Introducing Smartcard
Enabled RADIUS Server”, The 2006 International Symposium on Collaborative
Technologies and Systems (CTS 2006) May 14-17, 2006, Las Vegas, Nevada, USA
- Pascal Urien and Mohamad Badra, Secure Access Modules
for Identity Protection over EAP-TLS - Smartcard Benefits for User Anonymity
in Wireless Infrastructures. SECRYPT 2006, International Conference on Security
and Cryptography., 7-10 August 2006, Setubal Portugal
- Urien, P, Pujolle ,G, “TEAPM Trusted EAP Module” ,
e-Smart2006, 21-23 septembre 2005, Sophia Antipolis, France
- Pascal Urien, Mesmin Dandjinou, Mohamad Badra, Introducing
Trusted EAP Module for Security Enhancement in WLANs and VPNs, IASTED International
Conference on Communication, Network, and Information Security, CNIS 2006,
October 9-11, 2006, MIT Faculty Club, Cambridge, Massachusetts, USA
.