EAP-TLS SMARTCARD Personalization
I-User's Electronic Identity (eID)
In a PKI environment, the Certification Authority
is identified by its root certificate (ca) and usually produces PKCS12
certificates, whose file extension is generally .p12 or .PFX.
In a wireless network secured by the EAP-TLS protocol, the user’s
electronic identity may be seen as a couple of two files, a pkcs12 certificate
(certp12.p12) and the Certification Authority (CA) certificate (ca.der).
II- Tools for certificates generation
Download the TLSID.zip which includes all scripts, that
are necessary, with OPENSSL, for certificates generation.
The script maketcert.bat
located in the MakeCert repertory generates a root certificate,
a server certificate, and a client certificate.
The DemoCert repertory stores all materials prevoiuly
generated for EAP-TLS smartcards tests.
III- Converting the user's eID into smartcard script.
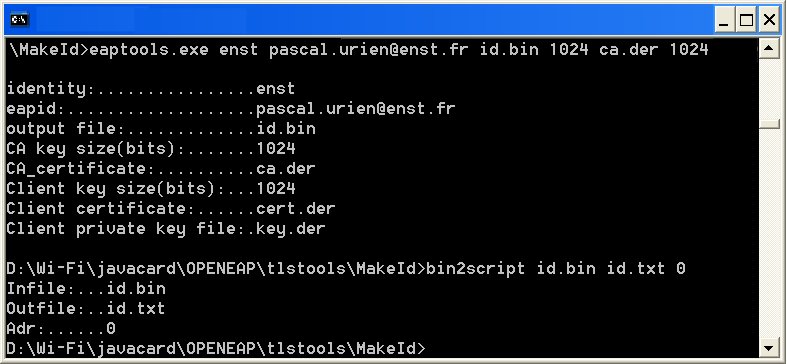
All these tools are located in the MakeId repertory of TLSID.zip.
MakeIDp12.bat converts the user's
eID (testclient.p12, ca.der) in a smartcard
script file (id.txt).
MakeID.bat
performs the same task, but work with PEM formats that are produced by
the OPENSSL software.
A smartcard script is a list of commands (ISO7816-4 orders) that are
executed by the EAP smartcard.
Two additional parameters are needed to generate a script for the EAP
smartcard,
* The user’s identity (enst in our example)
* The EAP-ID (pascal.urien@enst.fr
in our example).
IV- Downloading scripts to EAP Smartcards
Smartcard personalization is accomplished in typically
three steps.
1. Smartcard is protected by two PIN codes, one
is managed by the issuer and the other by the user.
The first script requires the issuer PIN, and modifies the default
user PIN.
2.The second script downloads the user converted
eID
3.Finally the third script sets the current smartcard
identity.
The device is ready for use.
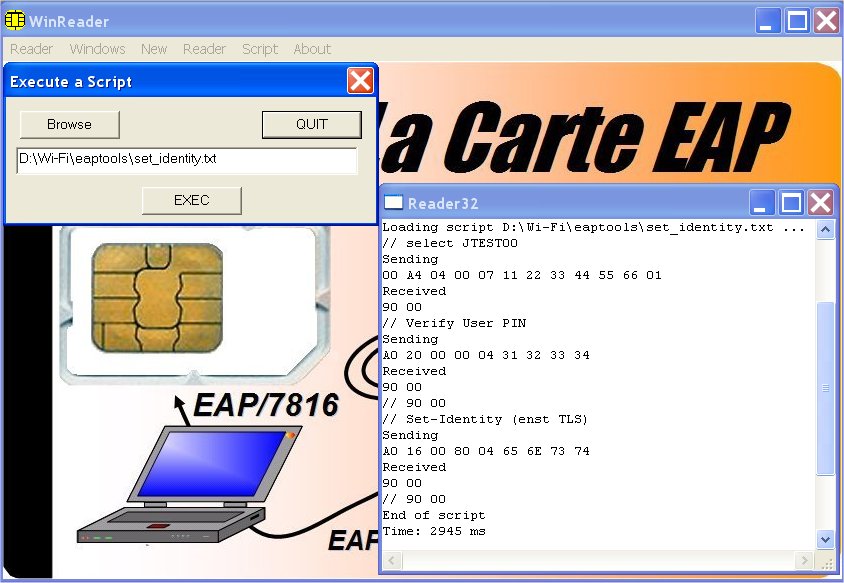
Get the set_identity.txt file.
Get the winreader.exe file